What's the password?
Managing the unmanageable
How easy is it actually for a criminal to figure out your online passwords and how can you stop this from happening? In this week’s blog I’ll unpack my own personal journey of password purification. Welcome to part 2 of the series around personal cyber security. My friends at the SA Insurance Crime Bureau (https://www.saicb.co.za) published this wonderful graphic last year to explain how easy it is for criminals to figure out your password.

In other words, if you have a password with less than 10 characters, without combining numbers, letters and symbols, you might as well just post the password on your social media pages along with your bank statements. Someone asked me in a talk I was doing a few weeks ago, “Tell me oh wise LiabilityGuy, how is it possible that a ten-digit password can be cracked so quickly?” They may not have said it exactly like that but actually it’s not as simple as hackers just letting a super computer program run, inputting millions of combinations although the technology is definitely available. This is because most, well-maintained websites will generally have lockout features so after a few guesses, the user will be prevented from more than say, 5 consecutive incorrect guesses.
So if the hacker only has 5 guesses at time to try a possible 10 billion combinations it would take a lifetime to derive the key. That is of course if the hackers were simply trying to access the database through the front-end login page. Incidentally, since I posted my previous article about my attempted hack a few weeks ago, there have been almost 1300 brute force attacks on this site. Those are attackers trying to guess my administration password.
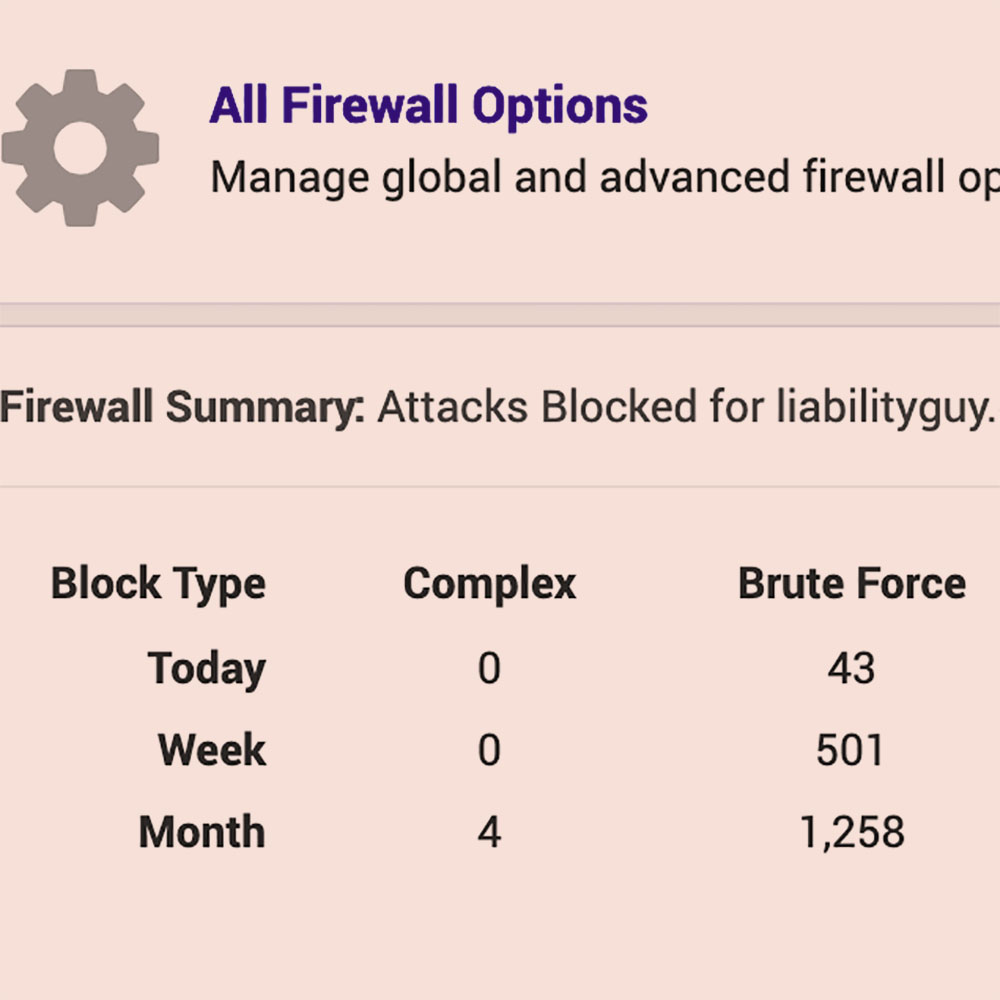
It is quite unrealistic to expect that hackers will try millions of passwords, waiting between lockouts, to get into a site. That’s like buying one cigarette at a time after each lockdown. Whenever you read about large-scale hacks, what has almost always happened is that hackers have stolen the entire database and then will use automated tools offline to “guess” the passwords in a copied database. Working offline they have as much time as they need to crack your well thought out password and username combo.
This brings me to the real reason for my blog. You see having a well-structured, complex password is only half the battle. Making sure that once it has been cracked, that it can’t be used in multiple attacks on other sites is the other half. If you reuse your password on many other sites, those brute force attacks become so much easier for the cyber criminals.
Credential re-use is a huge problem amongst internet users. Depending on which survey you look at, the range of lazy internet users who reuse their passwords is anywhere from 50% to 65%. Surprisingly a study done by DataProt in February 2021 showed that Gen Z users (age 16 to 24) are the biggest culprits with well over 70% using the same password and user combos across multiple sites.
The reason why we do this is simple, or rather it’s our need for simplicity that drives this reckless behaviour.
Even though I have some knowledge of cyber risk, I too have been guilty of this. In fact up until recently I would say that I was a habitual password regurgitator. I wonder if there is a support group for us? Fortunately this habit came to an end late in 2020 when I received one of those dreaded heads-up messages from Google to say the password I use on my account had turned up in one of the recent hack attacks.

This was the push that I needed to rethink my approach to my own cyber risk management. That inspirational moment was quickly followed by massive dread – how the hell would I remember which sites I have signed into over the years, let alone change the passwords?
A little LiabilityGuy disclaimer: I haven’t tried many methods but the one described below is working for me. If by the time you read this, I have subsequently been hacked…delete my profile from your memory and buy a typewriter and a telefax machine.
- If you use Mac OS then chances are you’ve allowed Safari to store your passwords in your keychain. You’ll have to sign into the Keychain with your mac password to see the list of sites and the user name, password combos. This was the category I was in.
- If you use Firefox, Chrome, MS Edge or Internet Explorer you may have allowed your browser to store the passwords. Those can all be found by clicking on the settings in the browser and then going to the security and passwords section. Easy.
- If you use Internet Explorer may I suggest you seek help from a mental health professional and join the 21st century as soon as possible. Just kidding, there is actually a video here
- If you haven’t allowed your browser to store your passwords then the only option available to you is to mine through your old emails and search for account registration emails that have been sent over the years. Try using phrases like “account confirmation” or “registration email”. I also recommend drinking heavily if using this method.
Number 4 above is a very painful exercise but don’t let this deter you on your recovery journey from pathological password peddling. I had actually registered for many different online services over the past decade so I determined that all I really needed to do was focus on the ones I had used most frequently over the past few years. I figured that my credit cards expire every 3-4 years so that sort of data probably wouldn’t have much value on the older sites and I’d changed my physical address a few times in the longer time span. In other words, I perceived the risk as lower on those accounts and dismissed them.
I was pleasantly surprised that most of the password storage options in browsers these days do have features that allow you to generate unique random passwords, some will even tell you on which sites you have reused passwords. If you aren’t going to use a separate password manager app, these browser solutions may be enough for you to sleep at night.
For me, I just felt that having all my data sitting in the browser database (even if it is encrypted) didn’t feel like enough so I opted to use a standalone password manager app. There are many available online. If you want a list of the top ones you can check this site out.
After checking out the costs and features I settled on Last Pass – perhaps the term “Ease of Use” in the ranking, sold me on it. I haven’t tried the rest so please send me your thoughts if you choose another.
Once you have the list of sites and passwords you can load them into the password manager, then you have to visit each site and change the password to a more complex unique one generated by the app. Its a pain but less painful than having your identity, money or reputation stolen from you.
I think Password Managers are excellent because:
- You only need to remember 1 password. That’s the one you use when you start up your browser.
- You can set up multi-factor authentication to protect the password vault. So you can use your Google Authenticator or any of your other favourites.
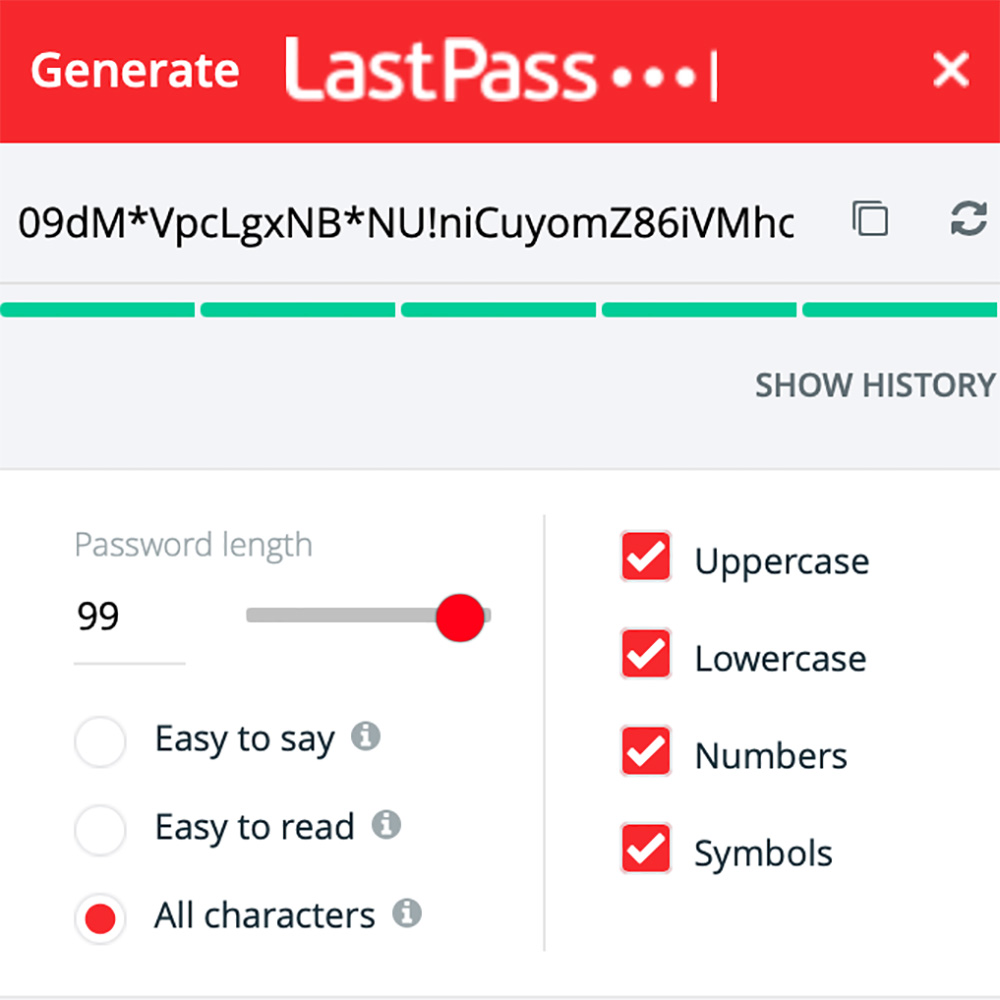
- You can use the password manager to generate random, extremely difficult passwords.
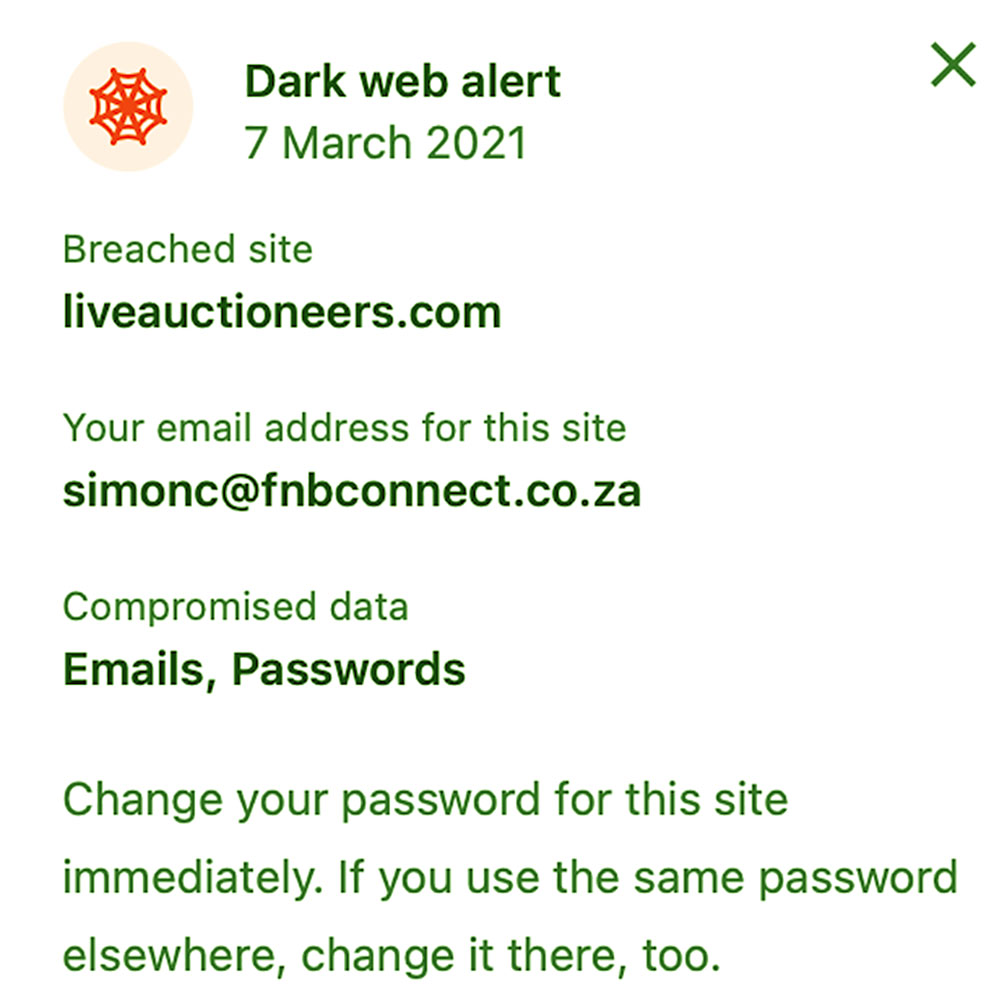
- They have dashboards that will alert you if any of your emails are compromised and appear on the dark web. Interestingly when I was doing this blog an alert came in today:
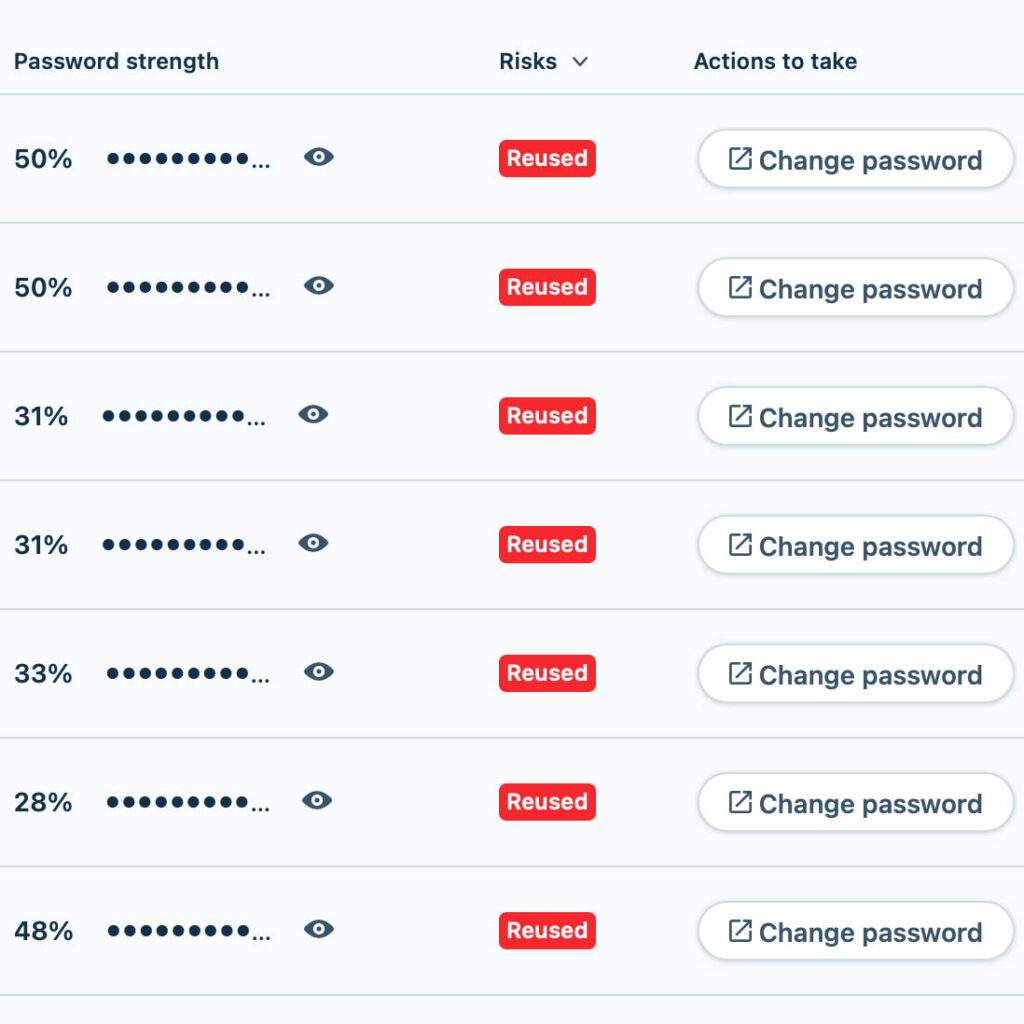
- You’ll be notified if you accidentally reuse your credentials again. You also get told if they are weak. Don’t take this personally. Just change them. Be strong.
It hasn’t all been plain sailing. I started the project in December 2020 whilst on holiday but quickly realised that it’s a mind numbing exercise to change all my passwords. Rather than doing it in one sitting I resorted to changing the core sites first and then slowly added the others as I logged into them over the subsequent months.
I also discovered that you need to turn off the autofill features in your browser after you load the password manager otherwise, old passwords get entered by accident and you get locked out of whatever site you are trying to access. This actually happened on one of my bank accounts and I had to go verify myself in person but that’s a story for another day.
I’ve completed the process now and I’d still give LastPass 8 out of 10 and I do believe I’m safer online now than when I started the exercise.
I’m the LiabilityGuy.
This article was originally called “what’s the $**&%# P@55word?” but the URL kept bombing out.